Thinking New Digital Business Model? Make sure you think about User-Side Risk

In light of the recent security breach fine imposed on British Airways, Joanne Moretti, Founder and CEO at JCurve Digital, explores the challenges with cybersecurity and suggests why, when it comes to security, a partner-approach rather than competition amidst players would be more beneficial for the end-'digital'-user
This week British Airways is facing a record £183 mn ($230 mn) fine for last year’s data breach affecting 500,000 customers. This fine represents approximately 1.5% of its current global revenues and while that sounds like a big “hit”, I believe it’s just the tip of the iceberg in terms of the damage brought on by the lack of proper security measures put in place to support new digital experiences and business models in general. The reputational backlash and lost opportunities will undoubtedly take a toll on income statement.
Incidents like the BA, are exactly what regulations like GDPR (General Data Protection Regulation) are trying to protect consumers from. In this case, the EU ICO (European Union’s Information Commissioners Office) confirmed that information including customer logins, names, addresses, payment-card information, and travel booking details were all compromised by poor security arrangements at the company.
 This hack was easily detectable and avoidable for that matter, according to Ivan Tsarynny, the CEO of Feroot, and a member of the GDPR Advisory Committee at Standard Council of Canada, as it was caused by an unauthorized change to JavaScript on BA’s web pages. In this age of digital commerce and seamless online experiences, continuous monitoring of all JavaScript, especially on login and transaction pages, has become absolutely essential.
This hack was easily detectable and avoidable for that matter, according to Ivan Tsarynny, the CEO of Feroot, and a member of the GDPR Advisory Committee at Standard Council of Canada, as it was caused by an unauthorized change to JavaScript on BA’s web pages. In this age of digital commerce and seamless online experiences, continuous monitoring of all JavaScript, especially on login and transaction pages, has become absolutely essential.
Ivan goes on to explain that “these attacks are known as ‘skimming’ and thousands are occurring every month. Skimming occurs when malicious code logs all the content the users enter through form fields which is captured by nefarious actors and routed to servers located elsewhere – generally put up for sale”. Ivan also noted that “skimming is becoming a more viable attack vector due to the proliferation of third-party software and marketing tools such as web trackers, analytics, tag managers, chatbots, chat services and ad tech tools.”
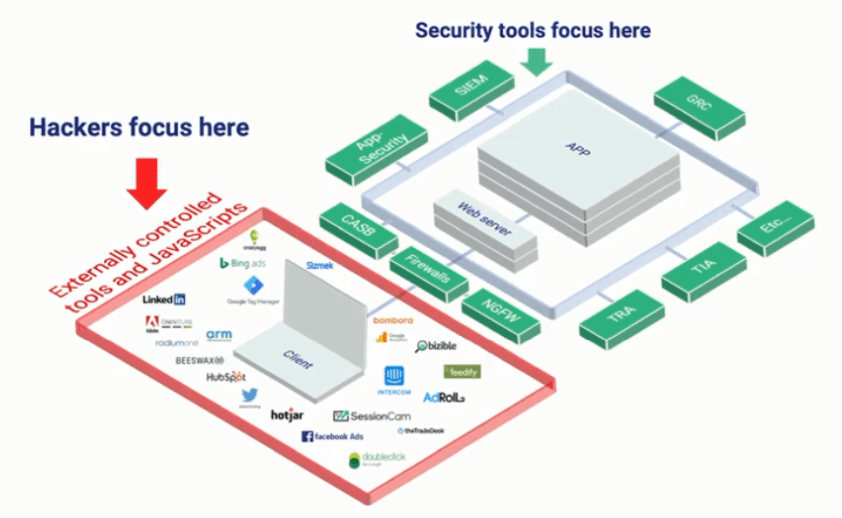 So basically, hackers are injecting a few lines of code into 3rd party JavaScripts that are loaded long before anything hits a firewall or security tool, to steal our personal information including credit card info, social security numbers, addresses, driver’s license information or any other personal info required to start or engage in a chat with a retailer, government agency, etc. The problem has now reached a fever pitch and Symantec reports it happens about 4,800 times a month across the globe - I personally believe that number is low. And because these malicious activities occur outside of the protected perimeter of an enterprise, on the user end of a transaction, it’s very difficult for companies to control them without some type of real-time monitoring and/or management tools in place.
So basically, hackers are injecting a few lines of code into 3rd party JavaScripts that are loaded long before anything hits a firewall or security tool, to steal our personal information including credit card info, social security numbers, addresses, driver’s license information or any other personal info required to start or engage in a chat with a retailer, government agency, etc. The problem has now reached a fever pitch and Symantec reports it happens about 4,800 times a month across the globe - I personally believe that number is low. And because these malicious activities occur outside of the protected perimeter of an enterprise, on the user end of a transaction, it’s very difficult for companies to control them without some type of real-time monitoring and/or management tools in place.
So, this is what led to data breaches at British Airways, Tickemaster and hundreds of other companies, and once again is happening every single day. It reminds me of the Target breach, but instead of the POS machine stripping off important info from credit cards, this type of “skimming” is occurring in real time, during a digital experience.

In further discussions with Ivan, I learned that Feroot is not only active in helping Canada deal with the current situation to put safety measures in place that protect consumers, their team have also developed a continuous user-side detection solution to resolve/avoid such attacks and prevent hefty fines in the process.
Obviously, with the EU imposing such gargantuan fines on companies who are targets of such malicious activity, Ivan sees opportunities to help these companies and government agencies, both in Europe and North America as well as supporting and enabling Security Service providers, systems integrators, and VARs through some type of white-label offering, such that they can deliver comprehensive security solutions. And frankly, that “ecosystem/partnership” approach is much smarter than a bunch of players trying to compete with one another. Given the pace and complexity of digital transformation and digital business, I just don’t believe in the word “competitor” any longer, especially in this war against cyber-crime; security firms must collaborate with one another and with their mutual customers to bring about solutions that will help us manage and mitigate risk effectively. This war isn’t one that will end anytime soon, and there is strength in numbers as far as I’m concerned.
What I found especially interesting, given my obsession with data and insights, and looking for ways to leverage it, is the data the Feroot tool can provide. Not only does it detect deviations, in an automated, real-time way through a single pane of glass approach, it can actually figure out where things came from and where data is going to in terms of country or region. So, if your customers’ data is going off to some server in China or Russia, it will track it down, and help you prevent it.
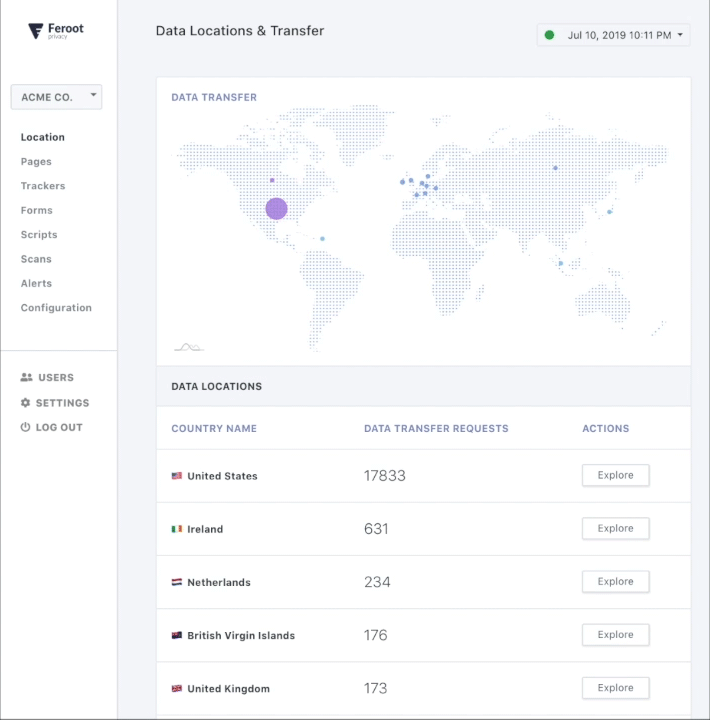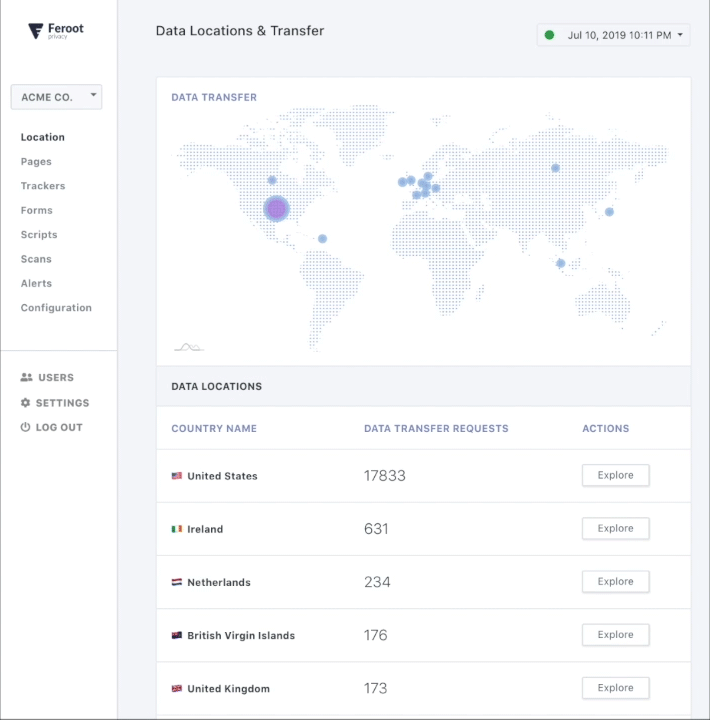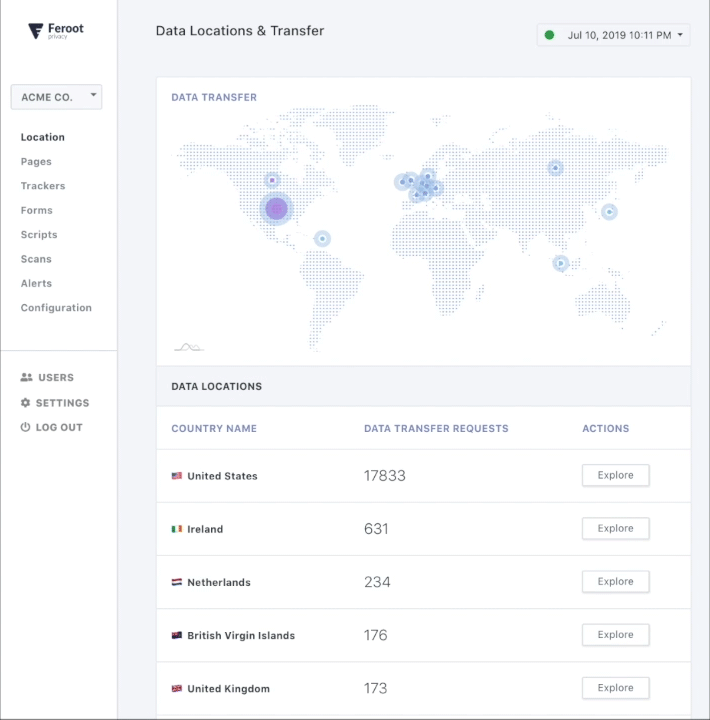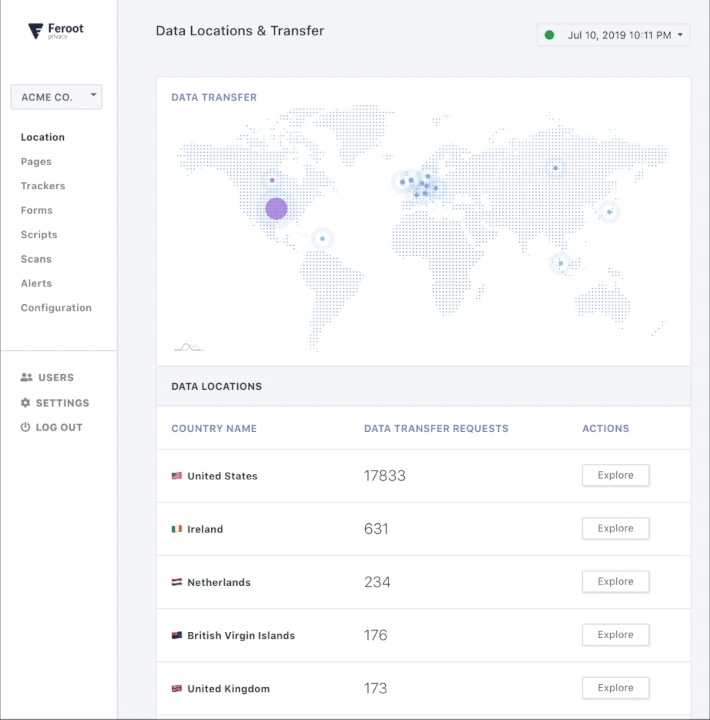
As a consumer who prefers online retail experiences over the hassle of brick and mortar experiences, I would feel much better shopping online or getting support from chat attendants, if something like Feroot were in place to ensure data security. Continuous user-side security monitoring systems like Feroot make it fairly simple to avoid these types of compromises and moreover the fines and reputational damages that go with it. Consumers want it, and regulators demand it, so definitely it’s something you must contemplate in your business and commercialization strategies when considering new digital business models.
This and many other digital transformation considerations are the things we at JCurve Digital see every day in helping customers bring new digital business models to market. And we’ve come to realize over the years, that security must never be an afterthought, but something that needs attention in the customer experience design process and requirements definition early and upfront. Not when its too late.


 By
By 








